MANAGED DETECTION AND RESPONSE
Gain complete control over cyber threats with our MDR platform. Secure, cross-platform coverage provides AI-driven threat detection, SOC-led incident response, rich security analytics, and 24/7 monitoring — all through one intuitive interface. Secure your data, minimize risk, and act quickly before a threat can cause damage.









Manage all alerts, investigations, and actions in one place. Stay on top of investigation tasks, track status, and ensure rapid threat response with minimal burden on your team.
Efficient.
Insightful.
Accurate.
Inside the MDR Engine
Explore how our MDR platform seamlessly processes security events — from real-time detection to automated triage and expert-driven decisions.


MDR Processes Security Events

Detection Engine generates security Alerts


Playbook Engine automates Alert enrichment and Triage:

ISSP

Client
The analyst reviews alerts and decides if client action is needed.
Oversees the entire process flow.

but engages only with specific analyses




Triage analysis complete;
Alert closed or Incident escalated.

Focus on what Matters

and Engage

Interactive alerts
View

Get a complete real-time view of your security landscape. Filter, sort, and analyze alerts for faster decision-making and precise response.




Deep dive into every alert

Consolidate all threat intelligence
in a unified workflow:
Structured incident metadata, automated task orchestration, analyses results, raw event data, forensic artifacts and detection outcome seamlessly integrated full situational context.
Empower your
security operations:
Accelerate incident triage, conduct deep investigations, and orchestrate response activities at scale through secure collaboration and actionable intelligence.

From Detection to Response
Analyze alerts and contextualize incidents with precision. Access everything from high-level threat summaries to detailed alert data in a unified view, enabling informed decisions, quicker investigations, and effective Incident Response.

Service Reliability & Health Monitoring
Our MDR platform continuously monitors the performance and health of all connected event sources—including endpoint sensors, network devices, and cloud connectors—to ensure uninterrupted telemetry flow and accurate, real-time threat detection across your entire infrastructure.
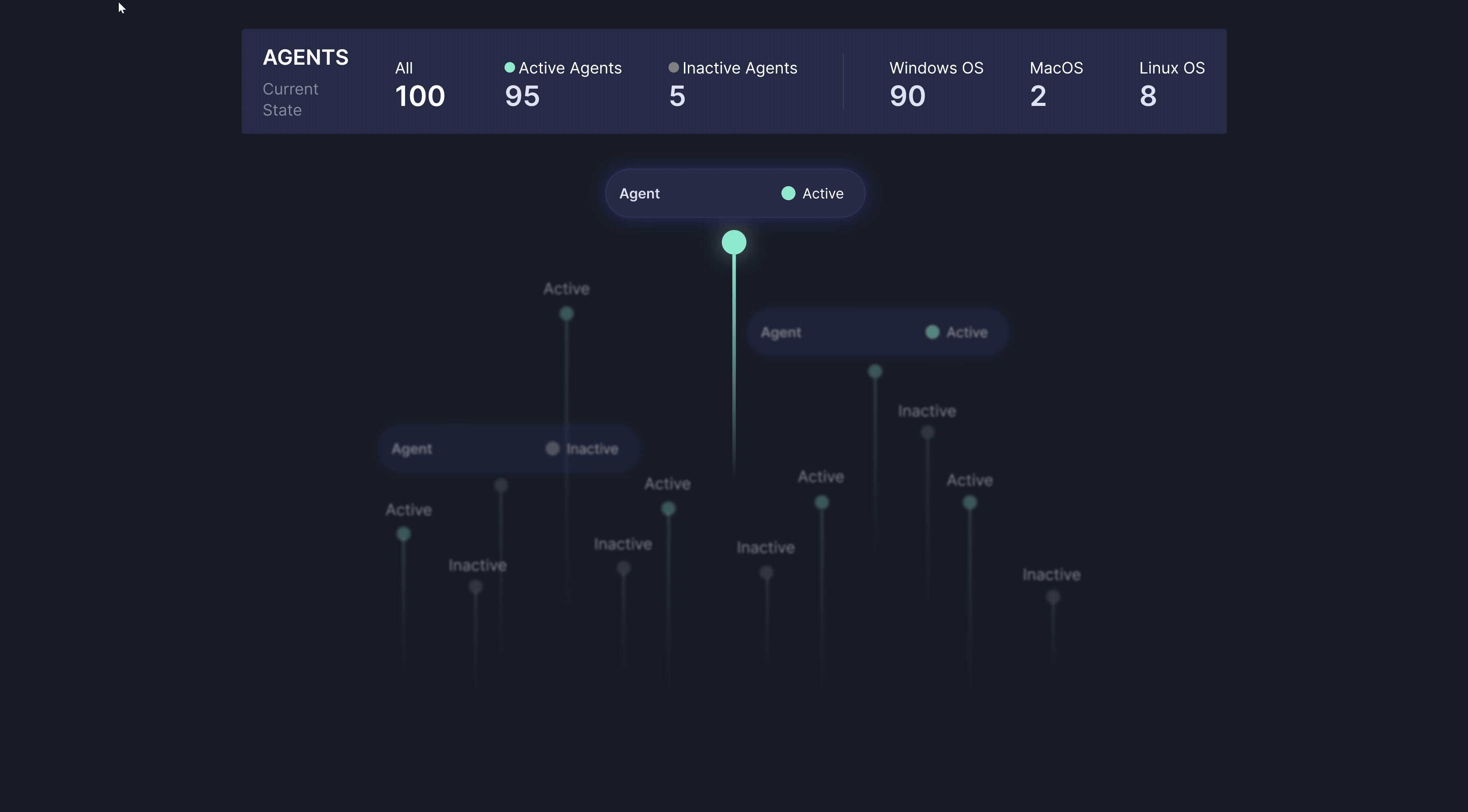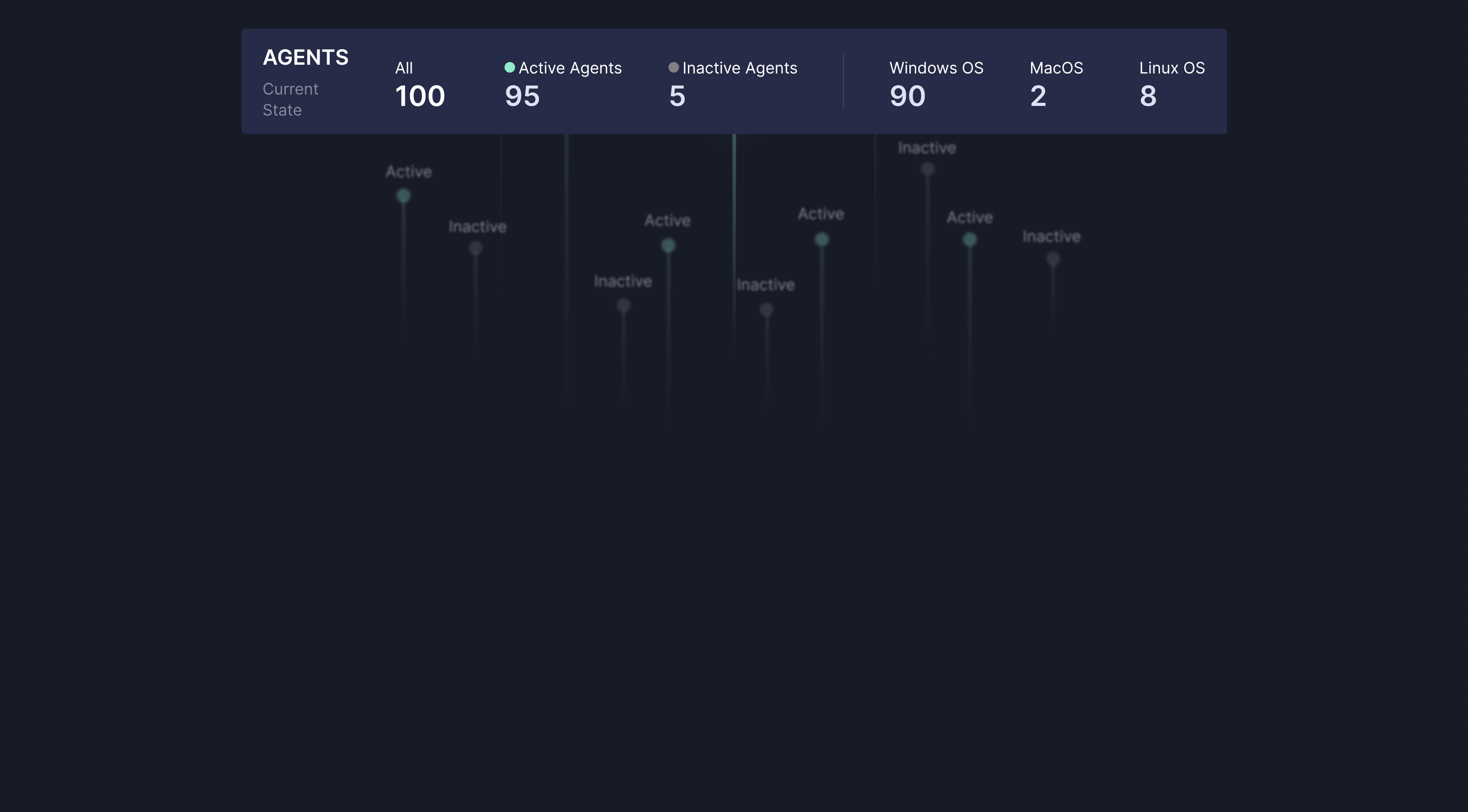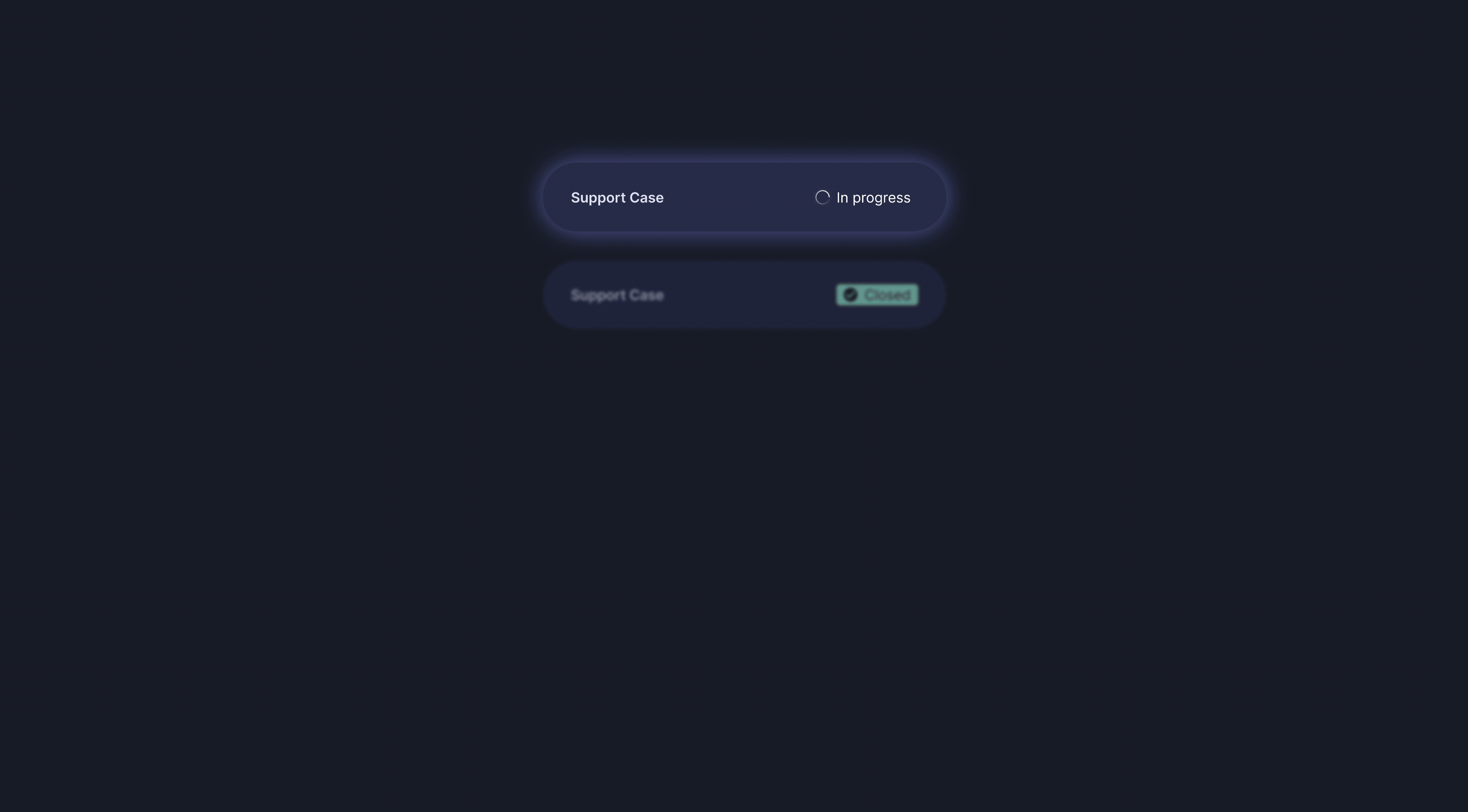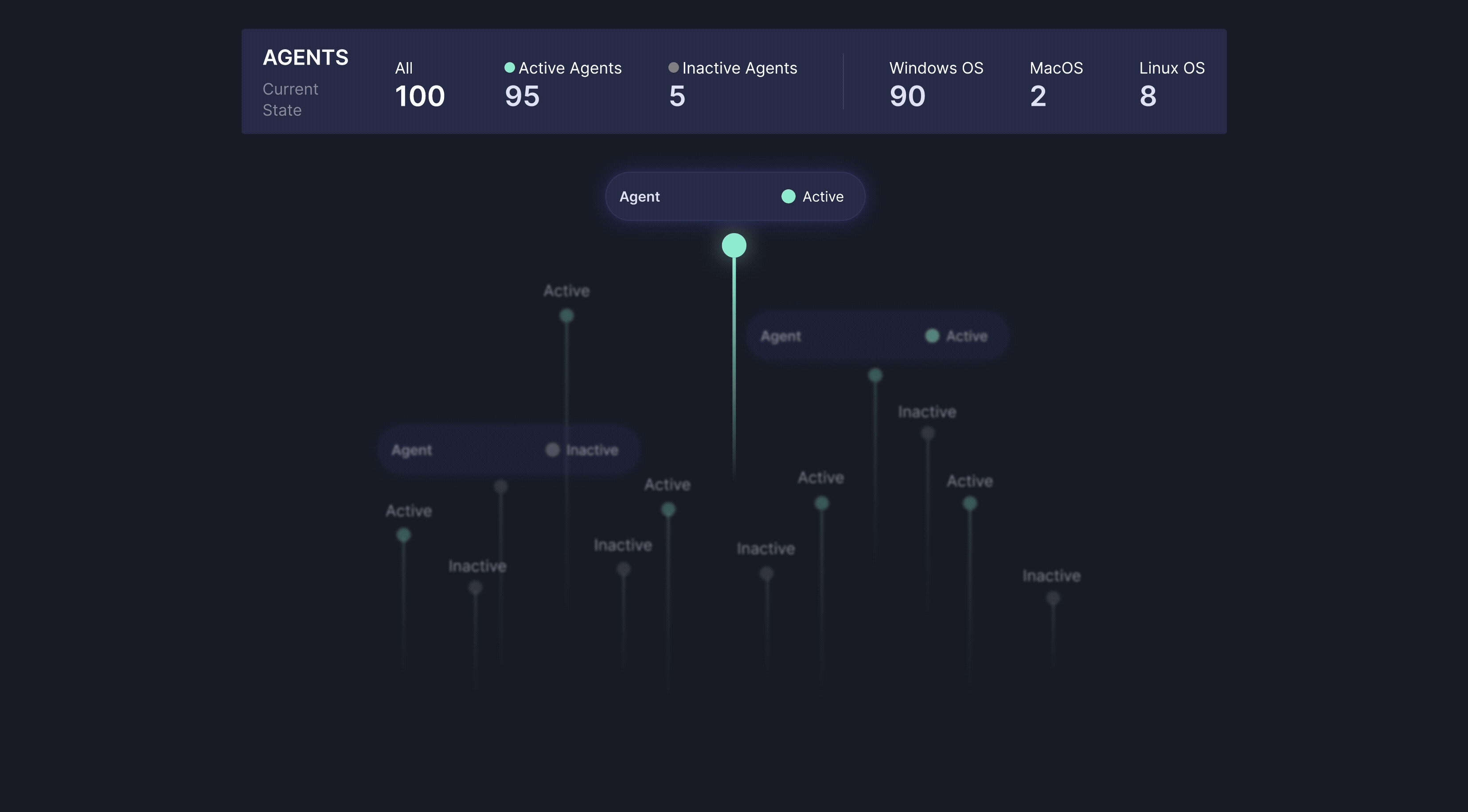
We track critical service metrics such as MTTD and MTTR, along with SLA compliance, to provide full visibility into the efficiency and reliability of our threat response. This continuous monitoring helps maintain strong security coverage while minimizing operational risk and downtime.
Support case handling is embedded directly within the platform, enabling seamless issue resolution and a stable service experience - all from a single interface.
Ready to Request a Quote?
Contact Us!
Tell us a little about yourself, and we'll be in touch right away!





